CDP flooding is a DoS attack using vulnerability of the CDP protocol, which is turned on by default on most of the Cisco devices. After the attack is started, the CPU of the target device is 100% saturated, preventing it’s normal operation. We will show how this attack can be launched and how to protect your devices against it.
CDP is a Cisco proprietary protocol. It is used to get information about directly connected devices, such as IOS, model, IP address, and so on. These messages are unencrypted, so if someone capture them, the attacker can obtain that information.
The attack that we will describe focuses on another vulnerability. In order to exchange the CDP information, the devices must establish a neighborhood. However, if a large number of neighborhood requests arrive to the device in short period of time, the processor runs out and stops managing common tasks.
Common device operation
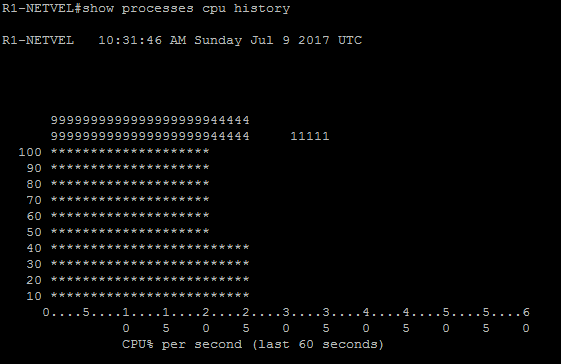
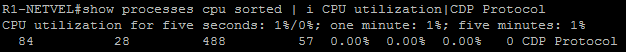
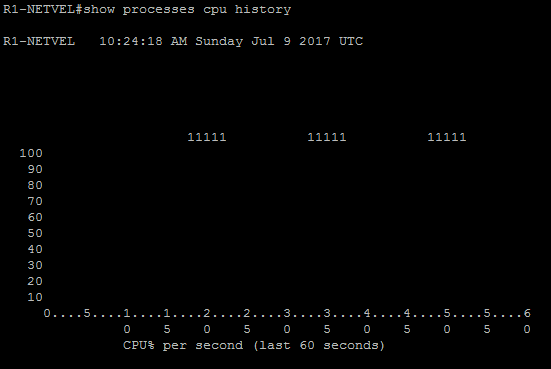
Below we can see what the router looks like before the attack begins. The router has no CDP neighbors and as no production runs through it, the processor is nearly 0% off.
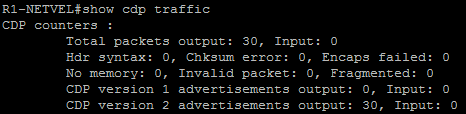
R1-NETVEL#show cdp traffic
R1-NETVEL#show cdp neighbors
R1-NETVEL#show processes cpu sorted | i CPU utilization|CDP Protocol
R1-NETVEL#show processes cpu history
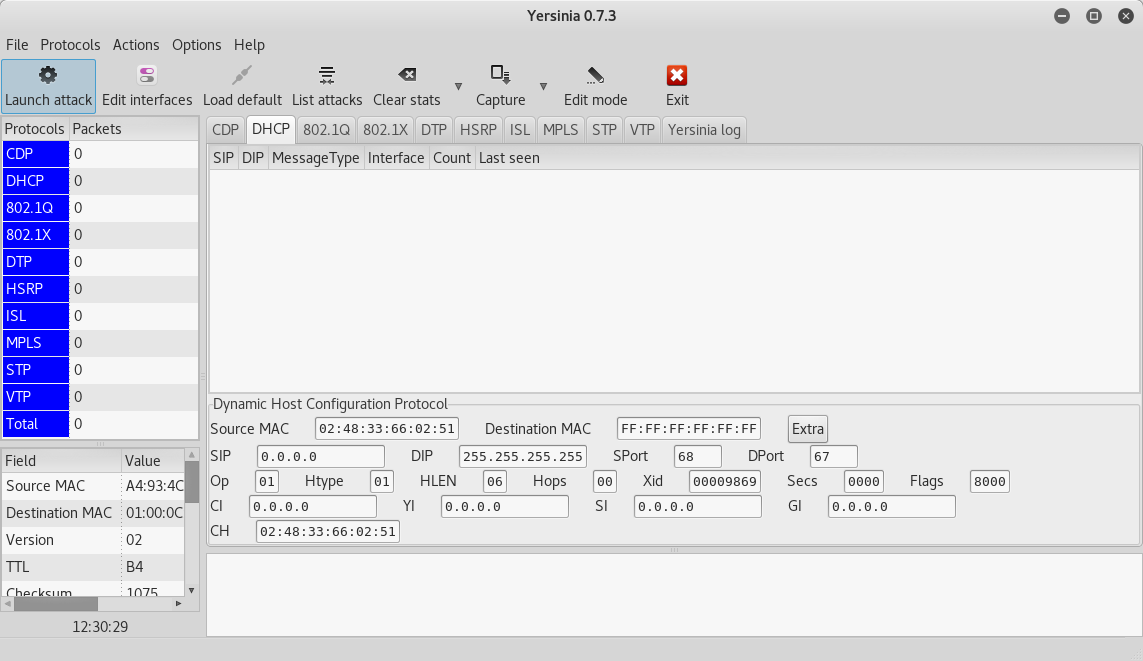
Launching CDP flooding
We will use the Yersinia tool located on the KALI Linux distribution as well as the other tutorials about Penetration Testing and Ethical Hacking.
We run Yersinia as follows:
root@kali:~#yersinia -G
Click on the CDP tab:
start: Launch attack -> flooding CDP table
stop: List attacks -> Cancel attack
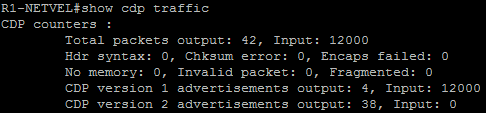
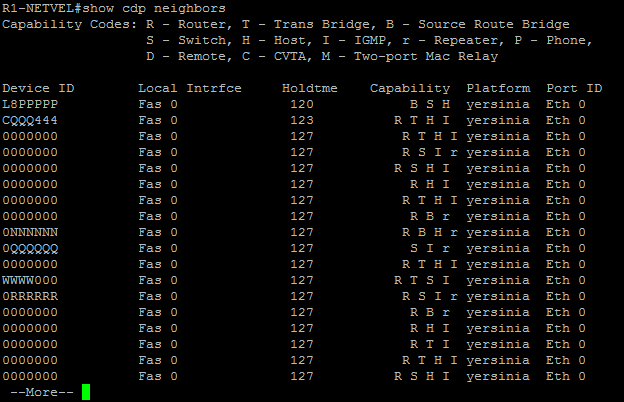
When we get back to the router, we’ll see that the router has set up a number of fake neighborhoods, which overloads the CPU. At this point, it is no longer able to handle common tasks.
R1-NETVEL#show cdp traffic
R1-NETVEL#show cdp neighbors
R1-NETVEL#show processes cpu sorted | i CPU utilization|CDP Protocol
![]()
R1-NETVEL#show processes cpu history

As we can see, the CDP contains very dangerous vulnerabilities, so it is recommended to disable this protocol whenever possible.
If we want to disable the CDP on the whole router, we can do this in the global configuration mode as follows:
R1-NETVEL(config)#no cdp run
If needed, we can only disable it on selected interfaces.
R1-NETVEL(config)#int fa0 R1-NETVEL(config-if)#no cdp enable